Computer network architecture graphics
from deck
IT Icons: Mobile & Smart Devices, Computer & Telecom Networks (PPT Template)
- Info
- How To Edit
- Usage example
Info
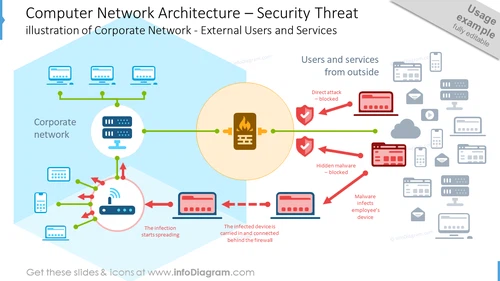
Computer Network Architecture – Security Threat
Slide Content
The slide illustrates various components and threats associated with Computer Network Architecture, focusing on security. The Corporate network is depicted at the center, connected to several devices. Direct attacks from outside are blocked, as indicated by the checked icons, symbolizing protection measures in place. However, an employee's device infected with malware has penetrated the network due to it being carried in and connected behind the firewall, showing that the threat originates internally. The infection then starts spreading within the corporate network, implying the vulnerability to internal threats.
Graphical Look
- The slide background features a soft blue gradient.
- The title of the slide is prominently displayed at the top in bold, dark text.
- There is a large, beige circle at the center representing a firewall.
- Inside the circle, a router or switch icon with a flame symbol illustrates the central point of the infection.
- A series of flat design icons represent various network devices such as laptops, a router, and a desktop computer, styled in blue and grey.
- Red arrows with flat design depict the spread of infection from the infected device to the corporate network.
- Red blocked icons and a green checkmark next to corresponding threats and defenses illustrate the status of each action.
- Text labels are used to describe different elements of the network and the actions, such as "Malware infects employee's device" and "Direct attack - blocked."
The slide is visually balanced with a clear flow of information from left to right. It uses contrast to distinguish between the safe areas of the network and the points of security breach.
Use Cases
- To explain the risks of internal security breaches in cybersecurity training.
- For showcasing security protocols and their effectiveness in preventing external attacks during IT and network security presentations.
- To discuss the need for secure practices by employees when bringing in personal devices for a company's security policy update.
- In a risk assessment meeting to visualize potential vulnerability points and discuss improvement in security measures. I'm sorry, but there was an error and the image was not processed correctly. If you would need any more assistance or have any other questions, please let me know!
How To Edit
How to edit text & colors
How to expand / shorten diagram
How to Replace Icons in infoDiagram PPT